Millennium Engineering & Integration Services Revenue, Growth & Competitor Profile
DBA AXIENT LLC
DBA MILLENNIUM
DBA MILLENNIUM ENGINEERING AND INTEGRATION CO.
DBA MILLENNIUM-VERSAR SERVICES LLC



Note: Revenues for privately held companies are statistical evaluations.
Millennium Engineering & Integration Services's Annual Report & Profile shows critical firmographic facts:
Note: Millennium Engineering & Integration Services's revenues are gauged from an analysis of company filings.
See all trademarks and details in the Full Report.
DBA MILLENNIUM
DBA MILLENNIUM ENGINEERING AND INTEGRATION CO.
DBA MILLENNIUM-VERSAR SERVICES LLC
Last updated:
Company Awards
Fast Growing

Big Fish

Brain Power (IP)

Company Profile & Annual Report for Millennium Engineering & Integration Services
Access the complete profile.Millennium Engineering & Integration Services Fast Facts
| Revenue | $100 - $500 million See Exact Annual Revenue |
|---|---|
| Employees | 100 - 500Exact Company Size |
| Primary Industry | 54133 Engineering Services |
| Additional NAICS Codes | 23622 Commercial & Institutional Building Construction 5417 Scientific Research & Development Services |
| Address | 1400 Crystal Dr Ste 800 Arlington, VA 22202 |
- What is the company's size? (Annual sales and employees)
- Millennium Engineering & Integration Services's annual revenues are $100 - $500 million (see exact revenue data)
- What industry is the company in?
- Millennium Engineering & Integration Services is classified as operating in the Engineering Services industry, NAICS Code 54133.
Millennium Engineering & Integration Services Annual Revenue and Growth Rate
| Millennium Engineering & Integration Services | Revenue Est. ($ Million) | Growth Rate (%) | # Employees |
|---|---|---|---|
| 2023 | $100 - $500 million Details in Premium Report | ||
| 2022 | |||
| 2021 | |||
| 2020 | |||
| 2019 | |||
|
1-Year Growth Rate: 3-Year Growth Rate (CAGR): | 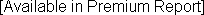 |
Note: Millennium Engineering & Integration Services's revenues are gauged from an analysis of company filings.
Millennium Engineering & Integration Services's Income Statement (based on Industry Averages)
| Millennium Engineering & Integration Services P&L | $ Millions |
|---|---|
| Revenue (Sales) | 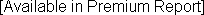 |
| Cost of Goods Sold | |
| Gross Profit | |
Operating Expenses | |
| Advertising | |
| Salaries and wages | |
| Other Operating Expenses | |
| Total Operating Expenses | |
| Operating Income | |
| EBITDA | |
| EBIT (Earnings Before Interest and Taxes) | |
| Net Profit | |
Trademark Applications
Trademark applications show the products and services that Millennium Engineering & Integration Services is developing and marketing. Millennium Engineering & Integration Services doesn't have any recent trademark applications, indicating Millennium Engineering & Integration Services is focusing on its existing business rather than expanding into new products and markets. Trademarks may include brand names, product names, logos and slogans.| Trademark | Date |
|---|---|
| SHADOWVIEW AGGREGATED TRACKING AS A SERVICE Computer monitoring service which tracks application software performance, performs periodic maintenance and provides reports and alerts concerning such performance; Maintenance of computer software relating to computer security and prevention of computer risks | 08/24/2022 |
| THREAT INFORMATICS CENTER TIC Research, development and engineering, installation, technical validation, maintenance and repair of computer software; Development of computer software for simulation of intrusion attacks; research, development and engineering of computer network, security software, technical validation of procedures for computer network security and related reporting thereon; consultation in the field of developing computer software, computer networks and information technology infrastructure; computer and data security consultation, namely, consultation in the field of assessment, detection, protection and security of computer data and electronic information, of computer networks, servers, applications, desktop computers and information technology infrastructure, all against attack, intrusion, unauthorized activity, misuse and other anomalous events; technical support services, namely, troubleshooting of problems in computer security networks and information technology infrastructures; computer and data security services, namely, analysis, evaluation, and testing of computer networks, servers, applications, desktop computers and information technology infrastructure for attack, intrusion, unauthorized activity, misuse and other anomalous events; computer and data security services, namely, identifying attacks, intrusions, unauthorized activities, misuses and anomalous events in computer networks, servers, applications, desktop computers and information technology infrastructure; computer and data security services, namely, remote monitoring of computer data information and computer networks, servers, applications, desktop computers and information technology infrastructure for detection of and protection against attack, intrusion and misuse and other anomalous events, including deployment of countermeasures in response to detection of unauthorized access or use of computer data and information, networks, servers, applications, desktop computers and information technology infrastructure; computer and data security services, namely, assessment of vulnerabilities of computer data and information, and computer networks, servers, applications, desktop computers and information technology infrastructure to attacks, intrusion, unauthorized activity, misuse and other anomalous events; computer and data security services, namely, providing early warnings, advisory alerts, notifications, and reports of attacks, security events, unauthorized activity, misuse and other anomalous events in a computer system or network, potential exploits and vulnerabilities for computer data and information, and computer networks, servers, applications, desktop computers and information technology infrastructure; conducting research in the field of computer and data security, namely, research relating to assessment of computer data and information, computer networks, servers, applications, desktop computers and information technology infrastructure to detect and protect against attack, intrusion, unauthorized activity, misuse and other anomalous events; Computer security services, namely monitoring computer networks for technical validation and reporting of computer network security and electronic information risks; Computer security services, namely, simulation of computer network security incidents; computer and data security services, namely providing computer security monitoring against vulnerabilities, attacks, intrusions, unauthorized activities, misuse and other anomalous events; validation of information in the nature of scientific research and analysis in the field of computer and data security, namely, vulnerability assessment and protection of computer data and electronic information, computer networks, servers, applications, and desktop computers and information technology infrastructure against vulnerabilities, attack, intrusion, unauthorized activity, misuse and other anomalous events | 09/03/2021 |
| THREAT INFORMATICS CENTER Research, development and engineering, installation, technical validation, maintenance and repair of computer software; Development of computer software for simulation of intrusion attacks; research, development and engineering of computer network, security software, technical validation of procedures for computer network security and related reporting thereon; consultation in the field of developing computer software, computer networks and information technology infrastructure; computer and data security consultation, namely, consultation in the field of assessment, detection, protection and security of computer data and electronic information, of computer networks, servers, applications, desktop computers and information technology infrastructure, all against attack, intrusion, unauthorized activity, misuse and other anomalous events; technical support services, namely, troubleshooting of problems in computer security networks and information technology infrastructures; computer and data security services, namely, analysis, evaluation, and testing of computer networks, servers, applications, desktop computers and information technology infrastructure for attack, intrusion, unauthorized activity, misuse and other anomalous events; computer and data security services, namely, identifying attacks, intrusions, unauthorized activities, misuses and anomalous events in computer networks, servers, applications, desktop computers and information technology infrastructure; computer and data security services, namely, remote monitoring of computer data information and computer networks, servers, applications, desktop computers and information technology infrastructure for detection of and protection against attack, intrusion and misuse and other anomalous events, including deployment of countermeasures in response to detection of unauthorized access or use of computer data and information, networks, servers, applications, desktop computers and information technology infrastructure; computer and data security services, namely, assessment of vulnerabilities of computer data and information, and computer networks, servers, applications, desktop computers and information technology infrastructure to attacks, intrusion, unauthorized activity, misuse and other anomalous events; computer and data security services, namely, providing early warnings, advisory alerts, notifications, and reports of attacks, security events, unauthorized activity, misuse and other anomalous events in a computer system or network, potential exploits and vulnerabilities for computer data and information, and computer networks, servers, applications, desktop computers and information technology infrastructure; conducting research in the field of computer and data security, namely, research relating to assessment of computer data and information, computer networks, servers, applications, desktop computers and information technology infrastructure to detect and protect against attack, intrusion, unauthorized activity, misuse and other anomalous events; Computer security services, namely monitoring computer networks for technical validation and reporting of computer network security and electronic information risks; Computer security services, namely, simulation of computer network security incidents; computer and data security services, namely providing computer security monitoring against vulnerabilities, attacks, intrusions, unauthorized activities, misuse and other anomalous events; validation of information in the nature of scientific research and analysis in the field of computer and data security, namely, vulnerability assessment and protection of computer data and electronic information, computer networks, servers, applications, and desktop computers and information technology infrastructure against vulnerabilities, attack, intrusion, unauthorized activity, misuse and other anomalous events | 09/03/2021 |
See all trademarks and details in the Full Report.
Market Share of Millennium Engineering & Integration Services's Largest Competitors
A competitive analysis shows these companies are in the same general field as Millennium Engineering & Integration Services, even though they may not compete head-to-head. These are the largest companies by revenue. However, they may not have the largest market share in this industry if they have diversified into other business lines. The "Competition" section of a business plan or investment memorandum would start by analyzing the information about these companies. Competitive advantage comes from offering better pricing or superior products/service.| Company | Headquarters | Revenue ($ MM) |
|---|---|---|
| CONSTELLATION NEWENERGY | Baltimore, MD | 100 |
| PERATON | Herndon, VA | 40 |
| WSP USA BUILDINGS | New York, NY | 25 |
| AMENTUM SERVICES | Germantown, MD | 24 |
| BELCAN | Cincinnati, OH | 22 |
| WSP USA | New York, NY | 21 |
| AECOM TECHNICAL SERVICES | San Antonio, TX | 16 |
| AMENTUM GOVERNMENT SERVICES PARENT HOLDING | Germantown, MD | 16 |
| STANTEC CONSULTING SERVICES | Chandler, AZ | 14 |
Nearby Competitors
These companies are similar in business line and location to Millennium Engineering & Integration Services. While some companies compete with neighboring businesses for customers, other companies may compete to attract skilled employees.| Company | Headquarters | Revenue ($ MM) |
|---|---|---|
| AMENTUM SPACEPORT | Arlington, VA | 100 |
| MILLENNIUM ENGINEERING & INTEGRATION SERVICES | Arlington, VA | 83 |
| REDHORSE | Arlington, VA | 53 |
| TECHNOMICS | Arlington, VA | 46 |
| STRATEGIC ANALYSIS | Arlington, VA | 35 |
| STRATEGIC INSIGHT | Arlington, VA | 29 |
Future Competition: Millennium Engineering & Integration Services's Fastest Growing Competitors
These companies are in the same general field as Millennium Engineering & Integration Services and are rapidly expanding. Companies may grow organically or through acquisition. In some cases apparently high growth rates may be caused by data that weren't available in previous years.| Company | Revenue ($ MM) |
|---|---|
 | |

 My Watch List
My Watch List